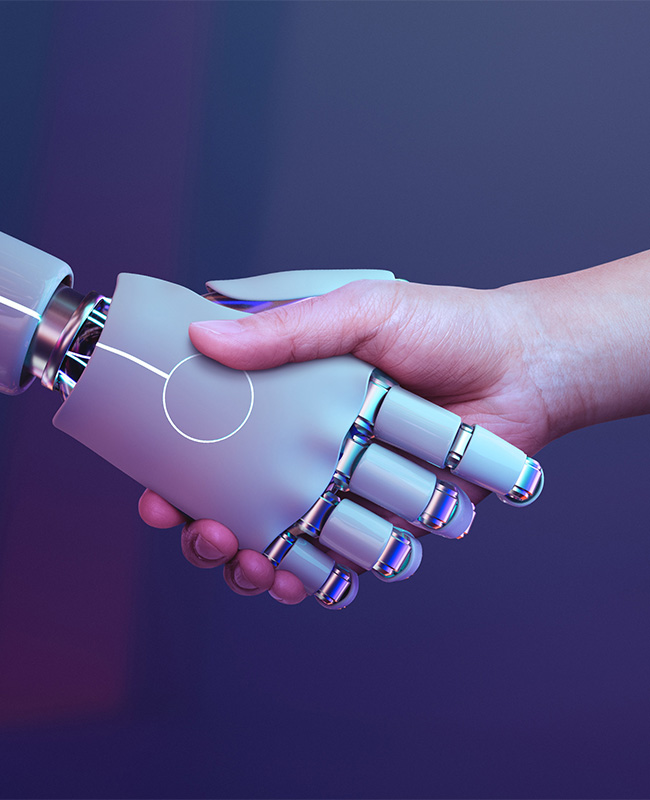
Your Security Operations Is In Your Hands Now
The Limit+ security operations program combines real-time monitoring, threat detection, incident response, 24/7 SOC Management and continuous improvement
We Provide Cyber Security That Works!
An effective cybersecurity operations program integrates DevSecOps and AI for automated threat detection, continuous monitoring, fast response, and proactive vulnerability management.
Our Approach Is Simple But Not Time-Wasting
-
Evolving Threat
The growing and evolving data security threats require advanced protection strategies to safeguard security operations
-
Widening Attack
The expanding digital and physical attack surface increases the data security attack surface, requiring enhanced protection and vigilance
-
Structural Weaknesses
Structural network, Data and Infrastructure Weaknesses expose organizations to breaches, highlighting the need for robust, proactive defense measures
Evolving Threat
The expanding digital landscape increases the enterprise security attack surface, requiring enhanced protection and vigilance
Learn More
Widening Attack
Lorem ipsum dolor sit amet, consecte adipi scing elit. Adipiscing eleifend dictum potentirder mattis viverra.
Learn More
Structural Weaknesses
Structural network, Data and Infrastructure Weaknesses expose organizations to breaches, highlighting the need for robust, proactive defense measures
Learn More
00K+
Cyber Security Projects
00
Customers Globally
00+
Cyber Security Experts
00%
Client Retention Rate
Expert Support To Enhance Your Cyber Defenses
Banking Security
Bank security services encompass measures to safeguard financial institutions against cyberattacks, fraud, and physical threats. These services ensure secure transactions, protect sensitive customer data, and maintain compliance with industry regulations.
- Focus on The Basics
- Educate Customers
- Be Proactive
- Tighten Internal Controls
Bank security solutions are essential for protecting financial institutions from evolving cyber threats, fraud, and physical risks. Effective solutions ensure secure operations, safeguard customer data, and maintain regulatory compliance and trust.

Manufacturing Security
Manufacturing security services protect facilities, assets, and personnel through surveillance, access control, cybersecurity, and risk management strategies.
- Focus on The Basics
- Educate Customers
- Be Proactive
- Tighten Internal Controls
Effective manufacturing security ensures operational continuity, protects assets, mitigates risks, and enhances safety through comprehensive strategies and advanced technologies.

Oil & Gas Security
Oil & gas security services safeguard critical infrastructure, assets, and personnel through surveillance, threat detection, risk management, and emergency response..
- Focus on The Basics
- Educate Customers
- Be Proactive
- Tighten Internal Controls
Oil & gas security ensures operational safety, protects assets, mitigates risks, and supports resilience through comprehensive strategies and advanced technologies.

Insurance Security
Insurance security services protect sensitive data, prevent fraud, ensure compliance, and mitigate risks through cybersecurity, surveillance, and risk management solutions.
- Focus on The Basics
- Educate Customers
- Be Proactive
- Tighten Internal Controls
Insurance security safeguards client data, prevents fraud, and ensures regulatory compliance, fostering trust and resilience in the insurance industry.

Healthcare Security
Healthcare security services protect patient data, safeguard facilities, ensure compliance, and mitigate risks through surveillance, access control, and cybersecurity measures.
- Focus on The Basics
- Educate Customers
- Be Proactive
- Tighten Internal Controls
Healthcare security ensures patient safety, protects sensitive data, and prevents threats, enabling smooth operations through robust physical and digital safeguards.

Future-proof Security & Infrastructure
Remote Workers
Remote worker security services include secure access, endpoint protection, monitoring, and training to mitigate cyber risks.
Security Advisory
Security advisory services enhance risk management, ensure compliance, improve incident response, and strengthen overall cybersecurity posture.
BCP/DR
BCP/DR ensures organizational resilience by planning for business continuity during disruptions, protecting critical data, enabling rapid recovery.
Application Security
Application security protects against vulnerabilities, ensures data integrity, prevents breaches, improves compliance, and enhances user trust.

24/7 Cybersecurity Operation Center
Our 24/7 cybersecurity operations services provide round-the-clock threat monitoring, real-time incident response, vulnerability management, and continuous security assessments to ensure comprehensive protection against evolving cyber threats.
- Malware Detection Removal
- Managing Cloud Security
- Content Delivery Network
- Testing Cyber Security
- Security Management
- Identifying Threats
- SIEM Threat Detection
- Server Security
- Website Hack Repair
- 24/7 Security Support
Explore Valuable Cybersecurity Resources
The Role of AI in Data Security
AI in cybersecurity enhances threat detection, automates responses, predicts vulnerabilities, improves incident management, and strengthens defenses against evolving cyber threats.
View Case Study DetailsThe Road To Recovery After A Cyber Data Hijack
The path to recovery after a cyber data hijack involves swift action, expert help, and strengthened security measures. Limit+ Emergency Cyber Incident Response Team can help you navigate through these challenges when they occur.
View Case Study DetailsThe Steps to Gaining Privileged Access Security
Breaching user access involves exploiting weak passwords, phishing, social engineering, or leveraging unpatched vulnerabilities to gain entry. Limit+ can find your gaps , mitigate it and prevent it from happening again.
View Case Study DetailsEnhance Trust, Compliance, And Governance
Enhance trust, compliance, and governance by implementing robust security measures, maintaining regulatory standards, and ensuring transparent, accountable data management practices.
View Case Study Details"Thanks to the 24/7 security operations program, we've experienced seamless protection, quick threat response, and complete peace of mind."

Jasica Lora - Security Lead
"AI-driven, DevSecOps security operations have significantly strengthened our defenses, automating threat detection and response while ensuring continuous, proactive protection."

Sarah Taylor - Developer
Get Privacy & Performance Tips, From The Experts
Compliance Management
Stay compliant with industry regulations through tailored security measures that meet all necessary standards.
Data Encryption
Ensure your data remains secure with robust encryption protocols for both storage and transmission.
Application Security
Application security protects against vulnerabilities, ensures data integrity, prevents breaches, improves compliance, and enhances user trust.
BCP/DR
BCP/DR ensures organizational resilience by planning for business continuity during disruptions, protecting critical data, enabling rapid recovery.
Security Advisory
Security advisory services enhance risk management, ensure compliance, improve incident response, and strengthen overall cybersecurity posture.